The most common applications in the user login, and some API data exchange scenarios.
I included some of the more classic PHP code encryption and decryption functions for everyone to share. Cryptographic principles generally through some encryption and decryption algorithms, the key is added to the algorithm, encryption and decryption finally get results.
1 Very awesome authcode encryption functions (with Detailed)
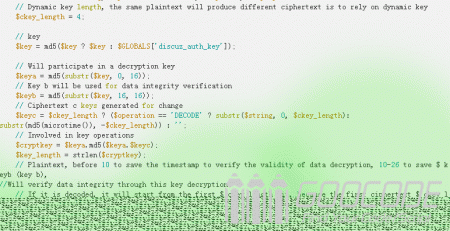
function authcode($string, $operation = 'DECODE', $key = '', $expiry = 0) {
// Dynamic key length, the same plaintext will produce different ciphertext is to rely on dynamic key
$ckey_length = 4;
// key
$key = md5($key ? $key : $GLOBALS['discuz_auth_key']);
// Will participate in a decryption key
$keya = md5(substr($key, 0, 16));
// Key b will be used for data integrity verification
$keyb = md5(substr($key, 16, 16));
// Ciphertext c keys generated for change
$keyc = $ckey_length ? ($operation == 'DECODE' ? substr($string, 0, $ckey_length):
substr(md5(microtime()), -$ckey_length)) : '';
// Involved in key operations
$cryptkey = $keya.md5($keya.$keyc);
$key_length = strlen($cryptkey);
// Plaintext, before 10 to save the timestamp to verify the validity of data decryption, 10-26 to save $ keyb (key b),
//Will verify data integrity through this key decryption
// If it is decoded, it will start from the first $ ckey_length bit, because the first ciphertext $ ckey_length-save dynamic key, in order to ensure the correct decryption
$string = $operation == 'DECODE' ? base64_decode(substr($string, $ckey_length)) :
sprintf('%010d', $expiry ? $expiry + time() : 0).substr(md5($string.$keyb), 0, 16).$string;
$string_length = strlen($string);
$result = '';
$box = range(0, 255);
$rndkey = array();
// Generate keys book
for($i = 0; $i <= 255; $i++) {
$rndkey[$i] = ord($cryptkey[$i % $key_length]);
}
// With a fixed algorithm, disrupting key book, increasing randomness, it seems very complicated, actually does not increase the intensity of the ciphertext
for($j = $i = 0; $i < 256; $i++) {
$j = ($j + $box[$i] + $rndkey[$i]) % 256;
$tmp = $box[$i];
$box[$i] = $box[$j];
$box[$j] = $tmp;
}
// Encryption and decryption core part
for($a = $j = $i = 0; $i < $string_length; $i++) {
$a = ($a + 1) % 256;
$j = ($j + $box[$a]) % 256;
$tmp = $box[$a];
$box[$a] = $box[$j];
$box[$j] = $tmp;
// Key results from the key book XOR, then into character
$result .= chr(ord($string[$i]) ^ ($box[($box[$a] + $box[$j]) % 256]));
}
if($operation == 'DECODE') {
// Validate data validation, see unencrypted plaintext format
if((substr($result, 0, 10) == 0 || substr($result, 0, 10) - time() > 0) &&
substr($result, 10, 16) == substr(md5(substr($result, 26).$keyb), 0, 16)) {
return substr($result, 26);
} else {
return '';
}
} else {
// The reason for the dynamic key stored in cipher text, which is why the same plaintext, ciphertext can produce different after decryption
// Because encrypted ciphertext may be some special characters, the replication process may be lost, so use base64 encoding
return $keyc.str_replace('=', '', base64_encode($result));
}
}
Function authcode ($ string, $ operation, $ key, $ expiry) of $ string: string, plain or cipher; $ operation: DECODE, said decryption, other representations encryption; $ key: Key; $ expiry: ciphertext expiration date.
Usage:
$str = 'abcdef';
$key = 'www.goocode.net';
echo authcode($str,'ENCODE',$key,0); //Encryption
$str = '56f4yER1DI2WTzWMqsfPpS9hwyoJnFP2MpC8SOhRrxO7BOk';
echo authcode($str,'DECODE',$key,0); //Decryption
2 the encryption and decryption functions encrypt ()
function encrypt($string,$operation,$key=''){
$key=md5($key);
$key_length=strlen($key);
$string=$operation=='D'?base64_decode($string):substr(md5($string.$key),0,8).$string;
$string_length=strlen($string);
$rndkey=$box=array();
$result='';
for($i=0;$i<=255;$i++){
$rndkey[$i]=ord($key[$i%$key_length]);
$box[$i]=$i;
}
for($j=$i=0;$i<256;$i++){
$j=($j+$box[$i]+$rndkey[$i])%256;
$tmp=$box[$i];
$box[$i]=$box[$j];
$box[$j]=$tmp;
}
for($a=$j=$i=0;$i<$string_length;$i++){
$a=($a+1)%256;
$j=($j+$box[$a])%256;
$tmp=$box[$a];
$box[$a]=$box[$j];
$box[$j]=$tmp;
$result.=chr(ord($string[$i])^($box[($box[$a]+$box[$j])%256]));
}
if($operation=='D'){
if(substr($result,0,8)==substr(md5(substr($result,8).$key),0,8)){
return substr($result,8);
}else{
return'';
}
}else{
return str_replace('=','',base64_encode($result));
}
}
Function encrypt ($ string, $ operation, $ key) in $ string: require encryption and decryption of string; $ operation: judgment is encryption or decryption, E is encryption, D represents the decryption; $ key: the key.
Usage:
$str = 'abc';
$key = 'www.goocode.net';
$token = encrypt($str, 'E', $key);
echo 'Encryption: '.encrypt($str, 'E', $key);
echo 'Decryption: '.encrypt($str, 'D', $key);